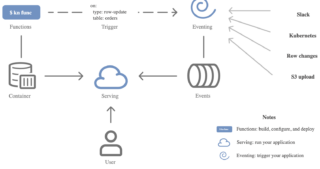
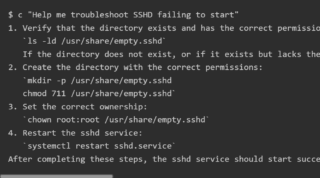
Mezmo Launches AI SRE for Root Cause Analysis
Mezmo, the active telemetry platform for AI agents, today launched its AI SRE (Site Reliability Engineering) agent for root cause analysis ahead of KubeCon, North America. The company’s secret sauce is context engineering, which supercharges AI agents with unmatched speed and precision. “We’ve built the fastest and most performant AI SRE in the world – …
How Platform Engineering Can Rescue DevOps from Kubernetes Complexity
While Kubernetes succeeded in reshaping how we think about infrastructure, it hasn’t eliminated the operational burden that comes with managing stateful services like databases. The very flexibility that makes Kubernetes so powerful has also given rise to sprawling toolchains, inconsistent patterns, and fragile integrations. For the DevOps tasked with keeping platforms stable and secure, Kubernetes …
Cloud Native Computing Foundation Announces Knative’s Graduation
The Cloud Native Computing Foundation (CNCF), which builds sustainable ecosystems for cloud native software, announced the graduation of Knative, a serverless, event-driven application layer on top of Kubernetes. Knative simplifies how developers build, deploy, and run modern workloads by abstracting the infrastructure concerns such as autoscaling, routing, event delivery, and building containers. It allows teams to focus on architecture …
Stop Chasing Breaches: Why Cloud Security Needs a Prevention-First Revolution
The cloud has transformed modern business. It delivers agility, scalability, and efficiency at a pace that was once unimaginable. Organizations can spin up infrastructure in hours, scale services in response to customer demand, and roll out innovations without the heavy capital expenditure once required. But with this transformation comes new risks, and securing cloud environments …
Latest News
This Week in AI Updates: Spacelift infrastructure provisioning, Grafana observability updates, ScienceLogic enhancements
Grafana Labs today announced the general availability of Grafana Assistant, a context-aware AI agent, along with the public preview of AI-powered Grafana Assistant Investigations, which extends Grafana Assistant to accelerate multi-step incident investigations. “AI is transforming every part of the software lifecycle, and observability is no exception,” said Tom Wilkie, CTO at Grafana Labs. “With Grafana Assistant …
Beyond Detection: Why Zero-Knowledge Proofs Are Our Best Defense Against Deepfakes in a Post-Truth World
The robocall seemed authentic enough. Last year, New Hampshire voters received what seemed to be President Biden discouraging them from participating in the primary election. Only it wasn’t Biden at all—it was a deepfake so convincing that election officials immediately launched an investigation. The incident reveals the fundamental inadequacy of our current approach to the …
Network Time-Series Analysis Beyond the LLM Hype
The rapid advancements in Artificial Intelligence (AI), particularly the ascent of Large Language Models (LLMs), have sparked widespread discussion about their potential to revolutionize various industries. Within network operations, where vast volumes of time-series data are generated continuously, there is a natural curiosity about whether LLMs can significantly enhance, or even replace, established analytical methods …
Database Performance on Kubernetes: Tradeoffs and Lessons Learned
Many infrastructure teams default to “put everything in containers.” Kubernetes makes it simple to deploy and manage services at scale, so databases often get pulled along for the ride. However, databases aren’t just another microservice. They rely on predictable performance from CPU, memory, storage, and networking – and containers can get in the way of …
It’s make or break for Agentic AI: Don’t repeat the mistakes of microservices past!
Technology has a worrying habit of repeating its architectural mistakes. Early struggles implementing microservices — where tight coupling masked as modular design and point-to-point integrations often just descended into complex webs — introduced failures that brought entire systems down. Today, we’re witnessing the same mistakes with Agentic AI integration. Agentic AI has huge benefits to …
Stop Feeding AI Junk: A Systematic Approach to Unstructured Data Ingestion
It’s go-time for enterprise AI. A PagerDuty global survey of 1,000 IT and business executives found that 62% of companies using agentic AI expect a return of 171% on average. Yet getting to ROI is no easy task. Recent surveys show mixed results on efforts thus far, with getting strategies right and making data “AI-ready” …
Progress Software updates Flowmon ADS (anomaly detection system)
Progress Software today announced the release of Progress Flowmon ADS 12.5, the latest version of its advanced anomaly detection system. Flowmon ADS 12.5 introduces AI-driven capabilities that give deep visibility into the network, enabling organizations to more rapidly detect any threats to the system and improve Mean Time to Repair, as well as for proactive …
Secure Code Warrior announces new solution that provides visibility and governance for AI coding tools
Secure Code Warrior is trying to provide organizations with greater visibility and control over developers’ use of AI coding tools with the launch of its new solution, Trust Agent: AI. This new offering tracks key signals that provide insights into how AI usage impacts software development risks. These include things like AI coding tool usage, …
Report: Only 12% of AIOps projects are fully deployed already, despite increasing investments
IT teams have been increasing their investments into AIOps initiatives, but a majority of these plans have yet to reach maturity. According to a new survey from Riverbed, only 12% of AI initiatives have been fully deployed and 62% are still in pilot or development stages. Despite these projects still largely being in development, 59% …
Sumo Logic launches Dojo AI to bring agentic AI to security operations
Sumo Logic is launching a new AI agent for tackling security operations. Dojo AI, powered by AWS, can automate routine tasks, streamline investigations, and free up security teams to work on other tasks. “At a time when every vendor is bringing new AI tools to market, the C-Suite is asking which agents can deliver measurable …
Learning Center
-
Webinars
Virtual Machines and Containers: Better Together | Live Webinar
LIVE: WED, SEP 24 | In the rapidly evolving landscape of Edge Computing, organizations face challenges including connectivity issues, limited on-site IT capabilities, and the need for secure and scalable solutions. Join us for this webinar, as we explore how the combination of Stratus’ ztC Edge platform and a Kubernetes management solution provides a comprehensive, …
-
Webinars
NetOps with Broadcom – Microwebinar Series
In this microwebinar series with Broadcom, Jeremy Rossbach, Chief Technical Evangelist for NetOps, provides essential insights and actionable strategies for network operations and explores practical strategies to enhance network resilience and accountability, achieve advanced visibility across hybrid environments, and transition from basic monitoring to comprehensive network observability for optimized performance. …
-
Webinars
AI’s Impact on Network Engineering and Operations – Microwebinar Series
AI’s Impact on Network Engineering and Operations Join Phil Gervasi from Kentik for this insightful 15-minute microwebinar where we will dive straight into the essential aspects of AI and uncover the practical realities of its application in network engineering, netops, and network architecture. …
-
White Papers
AI meets Network: Now what?
There’s a lot of buzz about AI in networking, but it can’t be real…right? Join our webinar where we’ll explore both the potential and the limitations of AI, providing a balanced view on its practical applications. By the end of this webinar, you’ll have a clear understanding of where AI can genuinely add value and …
-
Webinars
4 Requirements for a Single Pane of Glass in IT Operations
AVAILABLE NOW | For years, technology vendors have promoted the ‘single pane of glass’ as a silver bullet for service-oriented management. The promise was simple: buy this mega-suite of tools and get a single view of your IT environment. Unfortunately, the promise of a single pane of glass for IT operations and management has resulted …
-
Webinars
ITOps Times Live! Microwebinar Series – Internet Resilience
WATCH THE FULL SERIES Every business today relies on the Internet for critical business operations, and IT professionals must ensure Internet Resilience for their company’s customers and workforce. But what does that mean and how can they monitor everything in the digital delivery chain when so much is out of their control? The answer: Internet Performance …
ITOps Times Newswire
- Sonrai Security Introduces WALLy: The First AI Agent That Safely Fixes Cloud Privilege Risk
- Snowflake Unveils Cortex AI for Financial Services: Enterprise-Ready AI Built to Scale
- Mirantis Launches MCP AdaptiveOps for Agentic Infrastructure Adoption
- Eve Security Raises $3 Million Seed, Introduces Industry-First Agent-in-the-Loop
- Exabeam and Cribl Partner on Threat Detection with Next-Gen Data Pipelines
- Chaos engineering pioneer Gremlin launches AI-driven Reliability Intelligence
- Commvault Unveils Clumio Backtrack for Amazon DynamoDB, Reshaping Cloud-Native Database Recovery and Resilience
- Kentik Launches Cause Analysis to Bring Network Expertise to Every Infrastructure Engineer
- Commvault Extends Support to Red Hat OpenShift Virtualization Workloads for Enhanced, Cloud-Native Cyber Resilience
- Causely’s New Integration with Grafana Labs Goes Beyond Observability to Understandability
- Opsera and Lineaje Partner to Deliver Agentic AI-Powered Security at Scale
- ServiceNow to Extend Leading Agentic AI to Every Employee for Every Corner of the Business With Acquisition of Moveworks