Nick Carstensen, technical product evangelist at Graylog
Organizations of any size can create large amounts of logs, leaving them to require a tool to consolidate the logs in a centralized location. Graylog steps up to this challenge and provides an easy to use interface for your daily interactions to your logs.
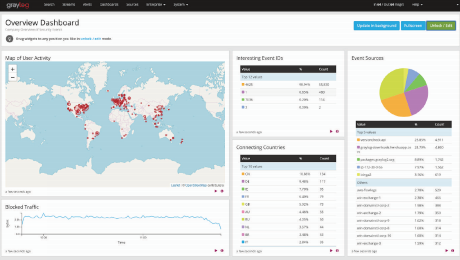
While you gather your logs, you want a solution to help organize them, make them human friendly for troubleshooting and provide different retention times to the logs based on your compliance or organizational needs. Having logs enriched with the correct data, like threat intelligence information, speeds up your investigation time for root cause analysis. Processing logs and putting them into useful visuals and dashboards make Graylog excel in usability.
RELATED CONTENT:
Log Management: A Guide for Buyers
A guide to log management tools
Alerting on your logs as they come in, increases your company’s awareness and allows for quick response to events which are happening on your network. These alerts can be security related or could be more operational and developmental. Having an alert sent out via an email or posted to a Slack channel will quickly let you keep up with your inflow of logs. Graylog’s correlation engine, can put together many different events to create one alarm, helping to reduce event fatigue plaguing many organizations.
Once an alert has been generated, use Graylog’s workflow features to help you quickly get to the information in a standardized method, usable by any analyst with access. Information can be exported from the system, or reports can be generated as well on an automated schedule for easy consumption.
With Graylog’s ability to ingest any type of logs created and its open message processing, the options for your logs are endless.








