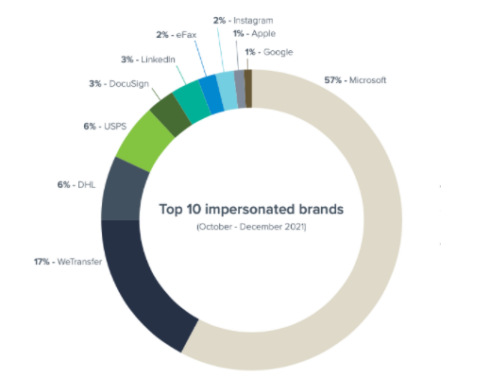
An average employee of a small business with less than 100 employees will receive 350% more social engineering attacks than an employee of a larger enterprise. The most commonly impersonated brand is Microsoft, used by cybercriminals in 57% of phishing attacks – the most prevalent social engineering attack of 2021.
These findings are from the report Spear Phishing: Top Trends and Threats, which was conducted by Barracuda Networks, a company that provides security, networking and storage products based on network appliances and cloud services.
Although larger organizations face a larger volume of attacks due to their size, the picture is reversed when it comes to the volume of attacks per email mailbox.
Cybercriminals find small businesses an attractive target because collectively they have a substantial economic value and they often lack security resources and expertise.
According to research by Cybersecurity Ventures, 60% of small businesses will close their doors six months after a security breach.
For years, security vendors have focused on protecting against email attacks, and the defense perimeters they built for customers have been effective at blocking most malicious or unwanted email messages, according to Barracuda’s report.
However, cybercriminals have shifted to more targeted attacks: from malware to social engineering, from operating as single hackers to forming organized criminal enterprises profiting from attacks that begin with a single phishing email.
“We see the growth in breaches because they work. Especially in an email, because anyone can send an email to anyone else, from anywhere in the world. As the security industry innovates and develops new defenses, so do the hackers,” Mike Flouton, the vice president of product management at Barracuda Networks told SD Times. “They evolve the way they target organizations to attempt to circumvent what security organizations have in place. Businesses need to be aware of the latest threat types and tactics used by cybercriminals and regularly assess their security stack to ensure they are fully protected.”
However, when brands are used in impersonation attacks, Microsoft and WeTransfer seem to be in the lead for tracking capabilities. Microsoft was used in 57% of phishing attacks, up significantly from 43% in July 2021.
Flouton said there are a couple of reasons for this. The popularity of Microsoft 365 is one the biggest drivers, and hackers impersonate Microsoft brands to steal business login credentials. Once they have them, they can get inside an account and inside the organizations and spread laterally, targeting business partners. As a result, sending phishing emails is a much easier way to breach security.
WeTransfer was the second most impersonated brand for phishing attacks at 17%. Often hackers used WeTransfer to host HTML files, which redirects their victims to a phishing site that again asks for Microsoft 365 login credentials in order to steal them.
“While preventing these attacks should be the number one priority, training is also a critical component. First, make sure users are aware of these types of threats. They should not log into the business account using a link from an email. Instead, advise them to go directly to the Microsoft 365 page to login. And always report suspicious emails and activities,” Flouton said.








