The machine identity management company Venafi is working to make it easier for companies to manage their cloud-native machine identities in Kubernetes environments. Today they released TLS Protect for Kubernetes within the Venafi Control Plane.
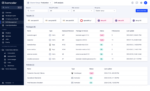
The new tool provides observability features that enable teams to identify security issues and be proactive in fixing those gaps. For example, the solution can identify all of the machine identities that are in use in an environment and shows the current status of workload certificates.
Teams can configure TLS Protect for Kubernetes to provide alerts on infrastructure health, compliance, and configuration.
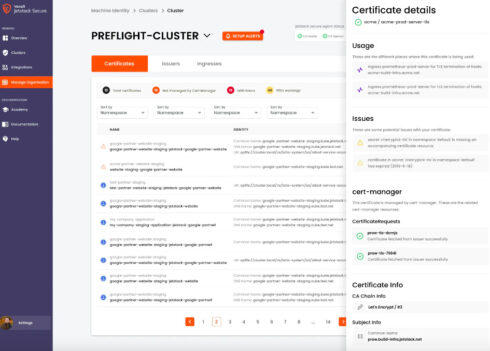
TLS Protect for Kubernetes incorporates the cert-manager project, which was designed by one of Venafi’s companies, Jetstack. This inclusion enables automation of TLS and mTLS certificate issuing and renewal.
Whenever a new cluster is created so is a new version of cert-manager to run alongside the cluster. This provides operators with better consistency across multi-cluster environments, the company explained.
The tool also provides multiple choices for deployments, with options for multi-cloud configurations, different cloud providers, and various Kubernetes distributions, as well as several integrations with popular secrets vaults and DevOps solutions.
“As organizations shift from traditional data center environments to modern, highly distributed cloud native infrastructures like Kubernetes, the volume of certificates and machine identities explodes, leading to increased threat risks and an increased need for security controls,” said Shivajee Samdarshi, chief product officer at Venafi. “Through the Venafi Control Plane, we’re modernizing machine identity management and making managing machine identities in cloud native environments easier than ever. TLS Protect for Kubernetes gives security and platform teams the observability, consistency and control over machine identities to ensure a validated and auditable chain of trust exists for every workload deployed to a Kubernetes cluster, including consistent approaches to certificate configurations and security policies.”