ITOps Times Open-Source Project of the Week: Cloud Custodian
Cloud Custodian is an open-source tool that provides cloud security, governance, and management. It enables IT operators to easily define rules for cloud infrastructure, allowing for increased security and reduced costs. It offers a single tool to replace many disparate tools and scripts. Policies are expressed in YAML and include the type of resource to … continue reading
ITOps Times news digest: Moogsoft and HCL Technologies partner, Sysdig Series F, and NeuVector expands partnership with IBM
Moogsoft and HCL Technologies have announced a new partnership to deliver an end-to-end solution for remediating IT incidents automatically. This new solution will combine features from the Moogsoft Observability Cloud and HCL DRYiCE iAutomate. Benefits to customers include assured continuity, maximized operational efficiency, and reduced support costs. “Today’s fully digital enterprise produces massive amounts of … continue reading
ITOps Times news digest: IBM storage portfolio updates, Red Hat Collaboratory expansion, and more
IBM has announced new updates to its storage portfolio. It announced an intention to release a container-native software defined storage solution called IBM Spectrum Fusion, which is expected later this year. The company also updated its IBM Elastic Storage System (ESS) solutions, including a redesigned ESS 5000 and the new ESS 320. “It’s clear that … continue reading
Anthos 1.7 comes with features to help anchor cloud journeys
Google has released the latest version of its managed application platform Anthos. Anthos 1.7 focuses on anchoring customers’ cloud journeys, creating a consistent operator experience, and establishing a familiar deployment target for developers. The company believes that cloud journeys should be anchored to a single cloud because rather than bringing their current state to a … continue reading
ITOps Times news digest: HackerOne’s new capabilities, Redis Enterprise extends support to Google Cloud Anthos, and Cisco AppDynamics new locations
HackerOne has announced new capabilities for detecting and remediating cloud misconfigurations. HackerOne vulnerability insights provide a snapshot of risk at a certain point in time. The company also added advanced workflows, remediation guidance, attestation reports, embedded submission forms, custom fields to gather more data from researchers, hacker communication, and hacker collaboration. Redis Enterprise extends support … continue reading
ITOps Times news digest: Dell EMC PowerStore updates, Mirantis Container Cloud updates, and FIDO Alliance’s new onboarding standard for IoT
Dell has announced updates to Dell EMC PowerStore. New features include intelligent data reduction, greater resiliency, and smarter tiering. In addition, it released the PowerStore 500, which is a lower-cost storage model. “PowerStore is the fastest-growing new architecture in Dell history. New and existing storage customers are seeing first-hand how its unique design, extreme performance … continue reading
Oracle Cloud Infrastructure now supported by ServiceNow
Oracle has announced a new integration with ServiceNow that will enable customers to access and manage Oracle Cloud Infrastructure (OCI) resources through their ServiceNow Service portal or ITOM Visibility application. This integration will provide customers with a single dashboard from which they can manage cloud resources from Oracle and other cloud providers. “Enterprise customers are … continue reading
ITOps Times news digest: Styra’s new compliance packs, expanded Azure Blob storage, and Guardicore’s new Zero Trust assessments
Styra has announced new compliance packs for its Declarative Authorization Service (DAS). The new packs are designed to bridge the gap between security and DevOps teams. New packs include a MITRE ATT&CK Matrix for Enterprise and CIS Kubernetes Benchmarks. The new packs consist of best practices from the OPA community. “To reduce security and compliance … continue reading
NVIDIA and other companies collaborate on AI-on-5G platform
NVIDIA has announced a new collaboration with Fujitsu, Google Cloud, Mavenir, Radisys, and Wind River. Together the companies will work to develop solutions for NVIDIA’s AI-on-5G platform and help accelerate the creation of smart cities, smart factories, advanced hospitals, and intelligent stores. “In this era of continuous, accelerated computing, network operators are looking to take … continue reading
NVIDIA releases Morpheus framework to detect security threats
NVIDIA has announced the release of its Morpheus framework that uses AI to detect and prevent security threats. It can detect leaks of unencrypted sensitive data, phishing attacks, and malware. According to NVIDIA, the Morpheus framework can be used together with NVIDIA AI computing and NVIDIA BlueField-3 DPUs to provide end-to-end protection. When used along … continue reading
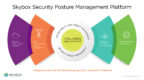
ITOps Times news digest: Skybox updates Security Posture Management Platform, Synopsys to acquire MorethanIP, and Red Hat and NEC announce collaboration
Skybox has announced updates to its Security Posture Management Platform. The platform enables IT teams to visualize and analyze their hybrid and multi-cloud networks to get a better sense of their attack surfaces. New capabilities include advanced analytics, optimized attack simulation, and increased dashboard customization. “Digital transformation demands a new approach to security posture management,” … continue reading
ITOps Times Open-Source Project of the Week: Kubesploit
CyberArk recently announced a new open-source project, Kubesploit, for testing Kubernetes environments. The goal of the project is to assist pen testers with performing comprehensive security assessments that mimic real-world attack scenarios, CyberArk explained. “To help protect Kubernetes clusters from attacks, we need to face the technology and the organizations being targeted. Yet, most of … continue reading