ITOps Times Open-Source Project of the Week: Instaclustr’s anomaly detection experiment
Detecting anomalies is crucial to the security of critical data, and Instaclustr just launched a new open-source project that will make it easier to detect those anomalies. The project was built out of a desire to see how far it could scale data-stack technologies like Apache Cassandra and Apache Kafka. It can be challenging to … continue reading
Kubernetes celebrates its fifth birthday, reflecting on its massive growth
The popular container orchestration tool Kubernetes is celebrating its fifth birthday today. It was first introduced by Google in June 2014, and it didn’t take long for others to see the potential of the tool. By August 2014, major companies such as Microsoft, Red Hat, IBM, Docker, and CoreOS had joined the Kubernetes community. “Kubernetes … continue reading
ITOps Times Blog: Edge computing will require massive changes in cloud infrastructure
Edge computing is still in its early days, but it will require massive changes in infrastructure before it will take off. Edge is another one of those terms that has many different definitions, especially at this early stage. But the most basic textbook definition of edge is one that encompasses the set of latency-sensitive applications, … continue reading
ITOps Times news digest: Red Hat OpenShift 4, Google Cloud’s compute pricing updates, and BMC’s new analytics and automation capabilities
Red Hat has announced the general release of OpenShift 4. In this release, Red Hat rearchitected the way that OpenShift gets installed, updated, and managed. It also introduced advanced day 2 management and automation. According to Red Hat, this release is all about bringing Kubernetes to the core of OpenShift. “As transformational as our open … continue reading
AIOps Manifesto lays out best practices for deploying AIOps
The newly created AIOps Exchange has just announced the release of its AIOps Manifesto. The AIOps Manifesto will provide best practices for deploying AIOps solutions. The paper was co-authored by experts from the AIOps Exchange steering community. The authors are requesting feedback on the manifesto, as well as open debate on the topics discussed. They … continue reading
ITOps Times news digest: Signal Sciences integrates with Cisco Threat Response, Red Hat Enterprise Linux 7.7 beta, and SentinelOne raises $120 million
Signal Sciences has announced a new integration with Cisco Threat Response in order to better help its customers defend against web app attacks. The integration will give customers instant visibility into their web application attack data, enabling security teams to respond to threats quickly. “In today’s evolving business landscape, we are seeing a dramatic shift … continue reading
ITOps Times news digest: Catchpoint DEX Sonar, Trifacta’s Snowflake integration, and AppDynamics’ new partner program
Catchpoint has announced a new solution that will bring together real user, active, and device monitoring into a single solution. DEX Sonar provides end-to-end visibility into the Digital Employee Experience (DEX), Catchpoint explained. “Employees are increasingly reliant on SaaS applications, so disruptions like outages or slowdowns equate to lost productivity, employee dissatisfaction, and potentially lost … continue reading
Survey finds security concerns are urging more companies to adopt SDN
Network security is at the top of most IT decision makers’ minds and security concerns may be driving organizations to adopt software-defined networking (SDN). Juniper Networks recently surveyed 500 IT decision makers to understand their SDN journeys. According to Juniper Networks’ survey, many organizations see security as a big consequence of not adopting SDN. Forty … continue reading
ITOps Times news digest: Linkerd 2.3.1 and OneLogin Accelerate growth
The latest version of the Kubernetes service mesh Linkerd is now available. Version 2.3.1 features proxy stability improvements. A few of the improvements include changes to the proxy’s routing behavior, a new dispatch time limit to limit the amount of time that a request can be buffered, and various bug fixes. Full release notes are … continue reading
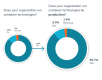
Report: Security is the biggest concern for those running containers
While container adoption continues to accelerate, companies continue to struggle with things like security and data management. Portworx’s annual Container Adoption Survey showed that 87 percent of respondents were running containers, which is up from just 55 percent in 2017 and from 80 percent in 2018. Of those, 90 percent were running containers in production. … continue reading
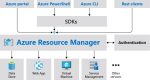
ITOps Times news digest: Azure Deployment Manager’s health checks, AWS CloudFormation update, and NGINX Unit 1.9
Microsoft announced new partnerships with service health monitoring companies in its Azure Deployment Manager. The Deployment Manager enables users to perform rollouts of resources on a region per region basis. Health checks for the service were announced at Build this year, allowing it to integrate with service health monitors to automatically stop deployment that are … continue reading
ITOps Times Open-Source Project of the Week: Terraform
HashiCorp’s open-source project Terraform is increasingly becoming more popular as organizations look for new ways to create and maintain infrastructure. Terraform is designed to write, plan and create infrastructure as code. In Thoughtworks’ latest technology radar, the company dubbed it the “de facto choice for creating and managing cloud infrastructures by writing declarative definitions.” While … continue reading