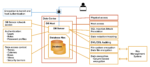
Cyber insurance: A crucial part of any cybersecurity strategy
The threat landscape has been expanding rapidly, and companies are under immense pressure to respond. A lot of companies are investing in trying to prevent attacks, but as evidenced by the massive influx of data breaches and cyberattacks, it’s impossible for a company to predict 100% of possible attacks. That’s where an emerging market is … continue reading
Why enterprises are running to the edge
The popularity of edge computing has greatly increased as more industries are adopting IoT devices and are increasing their demand for low-latency processing and real-time, automated decision-making solutions. Both the evolution of technologies surrounding edge computing, such as 5G, and the industry demand for its benefits, such as speed and low latency, have created a … continue reading
The lines between data center and campus networks are blurry
In tech, as in life, change is the only constant. From the days when all of our computer processing took place in mainframe terminals, to the decentralized shift to local servers, to the era of cloud computing, we’ve experienced one transformative wave of innovation after another over the past several decades. Today, we stand at … continue reading
How will augmented reality drive change in cybersecurity?
Augmented reality is a powerful technology with far-reaching implications. That said, there’s one sector in which it hasn’t yet reached its full potential: Cybersecurity. AR technology could bring about some incredibly positive changes, up to and including solving the talent shortage. I’d like you to imagine the following scenario. An automated intrusion detection system flags … continue reading
Is ITSM ready to manage the future’s AI infrastructure?
Artificial intelligence (AI) is maturing as a concept, and the excitement in the air is causing much anticipation of the potential fruit-bearing ahead. As conceived and hypothesized, the appeal of AI is complete automation of traditionally man-powered processes – all driven by patterns in data and machines’ “reaction” to it. Whether compete automation is achievable, … continue reading
Container security: 5 current trends you can’t afford to ignore
Enterprise confidence in containers continues to accelerate – not just in terms of the number of businesses now running containerized applications, but also in how many of those deployments span the entire application lifecycle. A recent survey by Market Cube finds that 87% of IT professionals are utilizing containers, and 90% of those are using … continue reading
Creating a multi-layered security architecture for your databases
Data security has never been more important than it is today. Considering the amount of data collection most modern apps require, it’s imperative to keep private and proprietary data safe and secure — and with measures like HIPAA, PCI DSS and the European Union’s GDPR, it’s also the law. Keeping databases secure from existing and … continue reading
Ensuring high availability and disaster recovery for SQL Server in the cloud
Failure is an option in IT, including in public clouds — despite their resilient, carrier-class infrastructures. And many of the failures that regularly cause downtime are excluded from the cloud service providers’ money-back service level agreement guarantees. For this reason, the customer, specifically the IT operations staff, is responsible for ensuring uptime for all SQL Server … continue reading
Network automation – To plan or not to plan is the question
“A man who does not plan long ahead will find trouble at his door.” – Confucius As the network evolves into a more dynamic environment due to the introduction of new concepts such as virtualization and software-defined everything, it is becoming imperative that operators automate as much as possible. Whether it be software-defined WAN, data … continue reading
5 ITSM trends and topics that will fuel digital transformation
Digital transformation is the buzzword that every CIO and most top-level managers are so concerned about. So, for all the hype around it, what is digital transformation, and is it really happening? Yes, it’s happening. With time, DX has become the driving force of businesses. Over the last few decades, the organizations that have disrupted … continue reading
IT Ops cost and digitization is accelerating retail industry move to cloud
Traditional retailers’ IT Ops teams are moving a greater percentage of their business-critical workloads from their datacenters to public clouds than their counterparts in other industries. The shift, a prevailing focus at last week’s annual National Retail Federation (NRF) show in New York, is poised to continue over the next few years. Various studies that … continue reading
premium Five considerations when moving toward cloud native
Building applications had rapidly become the easy part of development. Whether on the web or mobile, these applications need a place to live, and that place is constantly changing. From local servers in closets to colocation facilities to the cloud, we’ve seen rapid change over just the last few years. Now we have containers and … continue reading
Gartner: The future of infrastructure is always on, always available
The future of IT infrastructure is about being always on, and always available, everywhere, according to a presentation by Gartner at its IT Infrastructure, Operations and Cloud Strategies, held this week in Las Vegas. With applications so critical to business today, any outage could spell disaster for those companies, according to a number of conference … continue reading
premium Is security killing your digital transformation?
Hackers love traditional security. So do your competitors. Want to ruin their day? Forget what you know about how faster development increases risk. If your approach to security is slowing you down, it’s only a question of which you’ll lose faster—your data or your customers. To begin, let’s agree on one fundamental principle: In the … continue reading