Kyverno is a policy engine designed specifically for Kubernetes and the name means “govern” in Greek.
The management of policies in Kyverno is done through Kubernetes resources, eliminating the need for learning a new language to write policies. This approach enables the utilization of well-known tools like kubectl, git, and kustomize to handle policy management effectively.
Kyverno policies offer a broad range of capabilities, including validation, mutation, generation, and cleanup of Kubernetes resources. Additionally, they provide verification of image signatures and artifacts, contributing to enhancing the security of the software supply chain.
To ensure policy adherence and resource validation within a CI/CD pipeline, developers can employ the Kyverno CLI. This CLI tool facilitates policy testing and resource validation, enabling seamless integration into the continuous integration and delivery processes.
Kyverno enables cluster administrators to independently manage environment-specific configurations separate from workload configurations and implement optimal configuration practices for their clusters. They can also utilize Kyverno to examine existing workloads for adhering to best practices or employ it to enforce these practices by restricting or modifying API requests.
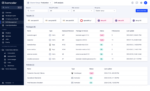
Kyverno operates as a dynamic admission controller within a Kubernetes cluster. It receives HTTP callbacks for validating and mutating admission webhooks from the Kubernetes API server and applies relevant policies to produce outcomes that uphold admission policies or decline requests. The policies in Kyverno have the ability to match resources based on various criteria such as the resource kind, name, label selectors, and other attributes.
Additional details on the project are available here.