Pulumi, an infrastructure as code (IaC) company, has announced several new capabilities that improve its cloud security and automation offerings.
The new capabilities include rotated secrets in Pulumi ESC, a new GitHub Action, a new Role-Base Access Control (RBAC) system, and new policy as code capabilities.
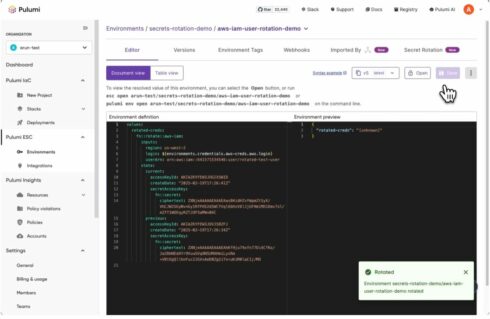
Secrets rotation
Secrets rotation will help companies ensure that they are not relying on long-lived credentials for their database passwords, API keys, IAM user credentials, and more. Teams will be able to set an automated rotation schedule or can trigger a secret rotation on-demand.
According to Pulumi, the rotated secrets function works by using a two-secret strategy where two secrets are valid at all times, which is helpful when multiple instances of an application share a credential, as it prevents instances being unavailable due to invalid credentials.
Secrets rotation also provides a full history of generated credentials, active credentials, and who is accessing them, and admins can notify teams trigger custom workflows, or trigger a Pulumi Deployment to update IaC stacks when a rotation occurs.
RELATED: The key to successful secrets management is to make the best way the easiest way
Pulumi ESC GitHub Action
The new GitHub Action allows Pulumi users to inject secrets and configurations into a GitHub Actions workload when they are needed, instead of having to store them indefinitely.
The integration also allows users to run any Pulumi ESC command from within the GitHub Actions workflow.
A new RBAC system
The new RBAC system (coming soon) allows customers to define specific roles with specific permissions to control who can access and modify resources, such as IaC stacks, ESC environments, and Insights accounts.
The system will also support role-based access tokens to ensure that automated processes also only have access to what is necessary to carry out their workflows.
New policy as code capabilities
Pulumi’s AI-powered infrastructure management platform, Pulumi Insights, now has new policy as code capabilities that allow it to automatically govern all cloud resources, even those that were discovered outside of IaC.
Customers can write policies once and apply them across IaC and all discovered resources in AWS, Azure, OCI, and Kubernetes.
The Pulumi Insights dashboard also displays all policy violations so that admins can quickly identify and fix them.
“This unified approach to policy enforcement marks a significant advancement in cloud security and compliance management, offering organizations a more streamlined and effective way to maintain their infrastructure standards,” the company wrote in an announcement.








