Datadog has extended its monitoring and analytics platform to security engineers with its new Security Monitoring solution, which will help break down silos between teams.
Key features in Security Monitoring include unified observability and security through over 400 integrations; real-time, out-of-the-box threat detection with turn-key threat Detection Rules; cost-effective data ingestion and analysis; customizable rule-editing; and context-rich security signals.
Datadog’s integrations enable users to collect metrics, logs, and traces from the entire stack as well as from security tools, offering end-to-end visibility into an environment, the company explained. For example, if there is abnormally high CPU utilization on a host, users can pinpoint which container or process is causing it to determine if there is a crypto-miner involved, Datadog explained.
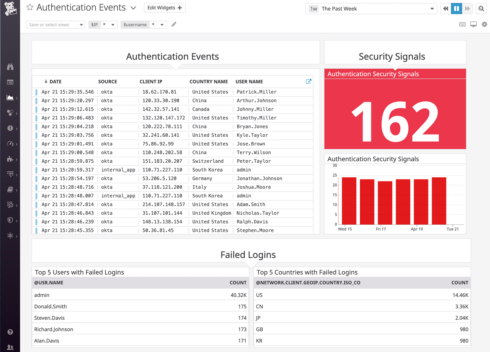
New security integrations also provide contextual information to help speed up investigations, such as with user authentication history from Okta or G Suite and network logs from integrations like Meraki.
“Companies undergoing the transformation of their security practices to adapt to more DevOps-friendly workflows are likely to look favorably on approaches that balance injecting security without disrupting those workflows,” said Fernando Montenegro, the Principal Analyst for Information Security, 451 Research, part of S&P Global Market Intelligence.
Datadog also retains security signals for 15 months so that teams can correlate them and identify trends over time. Teams can quickly filter signals by attributes like the MITRE ATT&CK® technique or any associated entities, and then pivot to other areas of Datadog for further investigation.
“We’ve built Datadog Security Monitoring to enable all engineers to cost-effectively analyze detailed observability data for potential threats, and easily collaborate during investigations,” said Marc Tremsal, the Director of Product Management at Datadog.
Additional details are available here.








