Topic: data
Cloudflare expands zero trust platform
Cloudflare announced several new capabilities for Cloudflare One, its Zero Trust SASE platform, including email security protection, data loss prevention tools, cloud access security broker (CASB), and private network discovery. “When I sit with customers, they share that one of the most daunting aspects of Zero Trust security is simply where to begin. Making matters … continue reading
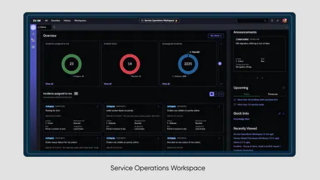
ServiceNow announces three new products
ServiceNow launched three new powerful products to advance digital business and drive innovation at scale. The first, Service Operations Workspace, offers tech services and operations teams a single space to manage work and to have shared visibility into issues. The second, App Engine Management Center (AEMC) provides structure and governance for low-code citizen developers. The … continue reading
ITOps Times Open-Source Project of the Week: Project Calico
Project Calico is a networking and network security solution for containers, virtual machines, and native host-based workloads. The project offers high performance with true cloud-native scalability by providing developers and cluster operators with capabilities across public cloud or on-prem, on a single node, or across a multi-thousand node cluster. It offers a choice of dataplanes … continue reading
Enhancing observability with AI in HCL Workload Automation
Organizations now are looking towards AI intelligence to help operators avoid manual operations, whether it’s due to the sheer number of alerts that they’re getting that are contributing to “alert fatigue” or the lack of observability of how the organization is working. HCL has introduced a new set of features to its HCL Workload Automation … continue reading
Kyndryl expands partnership with Dell to address cyber attack threats
IT infrastructure provider Kyndryl announced an expansion of its global alliance with Dell Technologies that focuses on helping customers use data optimization, infrastructure management services, and a cyber resilience solution to protect their critical business assets. Kyndryl provides Cyber Incident Recovery with Dell Technologies to accelerate cyber resilience for customers using Dell’s high-performance storage, servers, … continue reading
Google and other companies form Data Cloud Alliance
Google Cloud and other database providers in the tech industry announced that they are forming a new initiative to ensure that companies have more seamless insights and access into the data they need for digital transformation. “The proliferation of data, along with the many software and cloud-based applications used to analyze and manage it, means … continue reading
Context-aware detections available in Google Chronicle
Google announced the public preview of context-aware threat detections, alert prioritization, and risk scoring on Google Chronicle, which is a solution for threat detection. The new capability aims to help security professionals create efficiencies in customers’ threat detection and response. “An alert in isolation does not provide sufficient information, and associated metadata, context, and asset … continue reading
ITOps Times Open-Source Project of the Week: ValidKube
ValidKube combines open-source tools to help ensure Kubernetes YAML best practices, hygiene and security. The tool can verify your Kubernetes configuration files through kubeval, remove clutter from your Kubernetes manifests through kubectl-neat, and can scan YAML code for security vulnerabilities with trivy. RELATED CONTENT: Abstracting complexity from Kubernetes breaks down barrier to entry Kubeval uses … continue reading
BMC releases updates for data visibility and mainframe DevOps adoption
BMC announced new capabilities and integrations across its BMC AMI (Automated Mainframe Intelligence) and BMC Compuware portfolios that will help users improve service quality and accelerate software delivery. The company is aiming to enhance service quality with better data. The BMC Helix Discovery solution now automatically maps and visualizes service dependencies across mainframe and distributed … continue reading
ITOps Times Open-Source Project of the Week: Shotover
Shotover Proxy is an open source, high performance L7 data-layer proxy for controlling, managing and modifying the flow of database requests in transit. It can be used to solve many different operational and interoperability challenges for teams where polyglot persistence (many different databases) is common. Shotover can be deployed in many different ways including as … continue reading
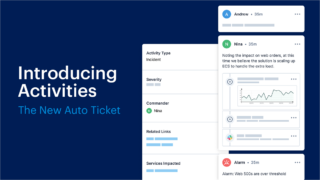
Transposit announces advanced ticketing capabilities to modernize ITSM
Connected workflow company Transposit announced Activities, which is a new feature that applies automation to ITSM processes. It provides a single source of truth across issues, incidents, and requests. Every action taken by both human and machine throughout any activity within the Transposit Timeline is captured through auto-tickets. Data and actionability are brought neatly together to … continue reading
ITOps news digest: AWS announces the availability of Amazon EC2 R6i instances, Red Hat bolters partnerships, IOTech partners with Google Cloud
The general availability of Amazon EC2 R6i instances are designed for memory-intensive workloads. Like M6i and C6i instances, these new R6i instances are built on the AWS Nitro System, building blocks that can offload a lot of the traditional virtualization functions to dedicated, delivering high performance, high availability, and highly secure cloud instances. The new … continue reading