Topic: security
ITOps Open-Source Project of the Week: Tungsten Fabric
This week’s open-source project of the week is a network virtualization platform for the cloud. Tungsten Fabric is an open-source scalable and multi cloud networking platform designed to provide a single point of control for networking and security observability and analytics. The project was originally hosted by Juniper Networks and known as OpenContrail. Juniper open … continue reading
ITOps news digest: Cloudflare’s Flan Scan, OneLogin’s support for AWS Session Tags, and OCF-over-Thread
Cloudflare is open sourcing its in-house lightweight network vulnerability scanner Flan Scan. According to the company, Flan Scan was created after unsuccessful attempts with industry standard scanners. “A little over a year ago, we were paying a big vendor for their scanner until we realized it was one of our highest security costs and many … continue reading
KubeCon: Securing Kubernetes with STRIDE
When you’re architecting your infrastructure around Kubernetes, you need to make sure you’re securing it properly. In a talk at this week’s KubeCon in San Diego, Pushkar Joglekar, security engineer at Visa, explained some of the best practices for securing Kubernetes. At Visa, the payment workflow boils down to: “Do it fast and with a … continue reading
ITOps news digest: Fairwinds Insights, RedisInsight, and StackRox Kubernetes security platform 3.0
Fairwinds new SaaS platform is launching a free public beta program. Fairwinds Insight is an open-source project for DevOps teams managing multiple Kubernetes clusters. The project is designed to give teams insight into any potential problems. According to the company, it can reduce the time it takes to research, learn and deploy Kubernetes auditing tools; … continue reading
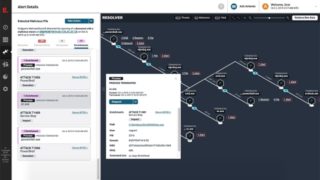
Sysdig Secure 3.0 provides Kubernetes-native threat prevention
Sysdig announced version 3.0 of Sysdig Secure, its tool that provides enterprises with threat prevention at runtime using Kubernetes-native pod security policies (PSPs). The new release introduces three new key features: Kubernetes Policy Advisor: which auto-generates PSPs to decrease the time spent configuring security, enabling teams to adjust misconfigurations before shifting to production. Falco … continue reading
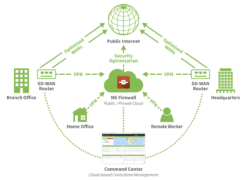
Untangle wants to bring network to edge with SD-WAN router and eSeries releases
Network security company Untangle announced that it is extending the network to the edge with the release of the Untangle SD-WAN Router and new eSeries appliances. The new Untangle SD-WAN Router allows users to to branch office networking to meet the needs of small offices with budget restrictions, the company explained. “Businesses are now commonly … continue reading
Microsoft releases Threat Experts to connect customers with security pros
Organizations face increasingly sophisticated attacks, whether that’s supply chain attacks, highly targeted campaigns or hands-on keyboard attacks. To address the issue, Microsoft launched Threat Experts within Microsoft Defender Advanced Threat Protection (ATP) to send targeted attack notifications and experts on demand. Defender ATP customers can now directly engage with Microsoft security analysts to understand how … continue reading
ITOps Times news digest: Elastic Endpoint Security, ManageEngine’s PAM360, and Radware Kubernetes Web Application Firewall
Elastic has released a new SIEM and endpoint security solution: Elastic Endpoint Security. The new solution is based on the company’s recent acquisition of Endgame, an endpoint threat prevention, detection and response provider. The solution will feature raw endpoint security data, event data, and alerts, in addition to the Elastic Stack’s existing logging, security, APM … continue reading
VMware completes acquisition of cloud-native endpoint protection provider Carbon Black
VMware has officially acquired Carbon Black for $2.1 billion. The company first announced plans to take on the cloud-native endpoint protection provider at the end of August. “Carbon Black brings us an industry-leading endpoint and workload security platform, with a cloud-native architecture, an AI-powered data lake and a smart, lightweight agent,” said Sanjay Poonen, chief … continue reading
Box and Splunk partner to provide enhanced threat detection capabilities
Cloud content management provider Box announced a new partnership to build integration between the “data-to-everything” platform provider Splunk and its security platform Box Shield. Box Shield is Box’s set of content security controls and advanced threat detection capabilities that is generally available this month. The controls are built natively into Box and designed to help … continue reading
Best practices for mitigating insider threats in the cloud
Although cloud vendors like Microsoft are generally responsible for protecting their infrastructures against attacks and even offer additional security services (e.g., the Microsoft 365 Security Center) to help customers with data protection, companies need their own controls as well. Why? Many different types of cloud users put corporate data at risk, including IT teams, managers … continue reading
Trend Micro introduces AI-powered email fraud detection feature
Cybersecurity company Trend Micro is trying to help companies better fight against identity fraud. Today, it released the latest version of its flagship security product, which includes a new AI-powered Fraud Buster feature that protects inboxes from scams and phishing attacks. According to Trend Micro, about 90 percent of the security threats it blocked in … continue reading