Topic: security
Report: Companies are overconfident in their cyber resilience abilities
A majority of companies believe they have the necessary technologies and processes in place to deal with security events in a timely manner, but new survey data shows that in practice, this isn’t the case. Cohesity surveyed 3,1000 IT and security decision makers for its Global Cyber Resilience Report 2024, and 78% of the respondents … continue reading
The C-suite conundrum: Are senior executives the Achilles’ heel of cybersecurity?
In today’s digital landscape, an organization’s C-suite and senior executives hold the most valuable corporate data and sign-off authorities, representing the highest potential risk over email. Whether it’s inbound spear phishing attacks or outbound mistakes resulting in a damaging data breach, the C-suite is vulnerable. But what do cybercriminals want from these individuals? Are breaches … continue reading
Q&A: The disconnect between the C-Suite and IT practitioners on AI readiness
Tech leaders are eager to reap the benefits of generative AI, but are they really production ready and able to be used in a secure way yet? According to Randall Degges, head of developer relations and community at Snyk, no. He joined us on the most recent episode of our weekly podcast, Get With IT, … continue reading
Report: Majority of security pros admit to using “shadow SaaS” apps
A recent survey from Next DLP revealed that over the last year, 73% of security professionals have used used “shadow Saas,” or SaaS applications not provided or approved by their IT teams. Further, even though they are using shadow SaaS, they admitted to being aware of the risks of doing so, with the most commonly … continue reading
Q&A: What the consolidation of the SIEM market means for IT
Over the last several months, multiple security information and event management (SIEM) platforms have either merged or been acquired. LogRhythm merged with Exabeam, Palo Alto Networks acquired IBM’s QRadar portfolio, and Cisco acquired Splunk. To talk about why this is happening and what it all means, Chas Clawson, field CTO at Sumo Logic, joined the … continue reading
Datadog releases a number of observability, security updates at DASH
Datadog is hosting its annual event, DASH, this week. At the event, the company showed off several new features across its entire platform, from observability to security. Observability Datadog LLM Observability allows customers to monitor their LLM apps to identify drifts in prompt topics and responses, mitigate prompt injections, detect personally identifiable information (PII) leakage, … continue reading
SELKS – ITOps Times Open Source Project of the Week
SELKS is an open-source network security monitoring platform that offers network intrusion and detection capabilities. The name comes from the original components it was built around: Suratica, Elasticsearch, Logstash, Kibana, and Scirius. It has since expanded to include EveBox, Arkime, and CyberChef as well. It can be installed on any Linux or Windows operating system … continue reading
Kyndryl Threat Insights provides security insights for AWS environments
Kyndryl has announced a new collaboration with AWS to provide its customers better insights into threats in their AWS environments. Kyndryl Threat Insights Managed Service provides a central repository for security data from AWS using Amazon Security Lake. By being able to access security data from a single view, companies will be able to uncover … continue reading
Puppet delivers enhanced infrastructure automation for a new operating reality
Infrastructure automation provider Puppet by Perforce has added new security, compliance, and continuous integration/continuous delivery (CI/CD) capabilities to its platform offering. Infrastructure resilience, improved agility and aligning with business goals are the critical focus for infrastructure and operations (I&O) leaders. According to a recent Gartner I&O Leaders Survey, the most important services I&O leaders need … continue reading
Report: Occurrence of specialized app attacks quickly rising
In the past year, the number of specialized attacks, which target specific applications through means such as making malicious changes to the code, has sharply risen. According to Digital.ai’s 2024 Application Security Threat Report, the likelihood of an iOS app having maliciously modified code grew from 6% to 20% in the last year. Similarly, for … continue reading
Trend Micro update helps organizations manage risks of AI adoption
Cybersecurity company Trend Micro this week released updates to its Trend Vision One solution designed to meet the mass adoption of new AI tools by managing the risks associated with that adoption and securing how organizations use AI. In the company announcement, co-founder and CEO Eva Chen said, “Great advancements in technology always come with … continue reading
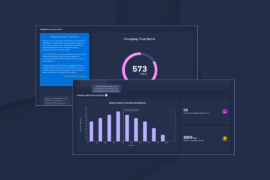
Secure Code Warrior’s new SCW Trust Score helps companies benchmark their security posture
The security learning company Secure Code Warrior is making it easier for organizations to assess the security posture of their development teams with the SCW Trust Score. The score utilizes 20 million data points from over 250,000 developers to provide a benchmark that teams can compare themselves to. Scores are given on a scale of … continue reading